I recently discovered RansomLord. It is a tool designed to defeat ransomware before they even try to encrypt your files. My goal here is to raise an alert in Wazuh whenever a DLL generated by RansomLord is accessed.
Step 1
Download RansomLord latest version from the repo. Right now it is RansomLord v3.1.
Step 2
Open a terminal and go to the directory where you saved RansomLord_v3.1.exe . Type RansomLord_v3.1.exe -a to display the 'About' screen.
Step 3
Now let's generate the trapped DLLs.
You can type RansomLord_v3.1.exe -i to display all the options and read a quick description. I chose to generate as many DLLs as possible.
Type the following command to launch RansomLord and validate with enter when asked : RansomLord_v3.1.exe -g *
Do not worry if you only have 12 files generated after this operation : some DLLs are used by several malwares. RansomLord has created 2 folders : x32 and x64. For the remaining steps, I chose to put all the files in the same folder.
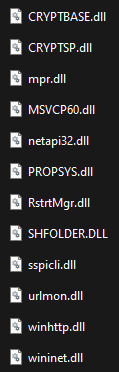
Step 4
This step is probably the most difficult. You have to move these DLLs somewhere in your disk or network where a ransomware would search. I did a quick search and read that most ransomwares are searching through the network first, so I created a folder on a network share with a name starting with an underscore to be sure this one will be accessed first.
Do NOT attempt replacing original Windows OS DLL files !
Step 5
Create a custom rule in Wazuh. I added this bloc in the local_rules.xml file :
<group name="RansomLord,">
<rule id="100057" level="15">
<if_sid>60003</if_sid>
<field name="win.system.providerName">^RansomLord$</field>
<field name="win.system.eventID">1</field>
<description>Activation d'une DLL piégée par RansomLord sur $(win.system.computer)</description>
<options>no_full_log</options>
</rule>
</group>Keep in mind that the number 100057 is for my own need, you should change it if you already have a 100057 custom rule in your file. Notice that if this rule is triggered, it will raise a level 15 alert.
Save the file and restart the wazuh-manager service.
Step 6
Now let's try to generate an alert. Every Windows OS has the rundll32.exe utility it will be very helpful. Let's use it to access a trapped DLL on a Wazuh endpoint. The syntax is :
rundll32.exe C:\Path\to\your\trapped\DLLs\trapped_DLL_name.dll,random_text_imitating_a_function_name
Example :
rundll32.exe C:\Tests\DLL\mpr.dll,HelloHowAreYou
This should immediately add a new entry in the Windows eventlog in the Application channel :
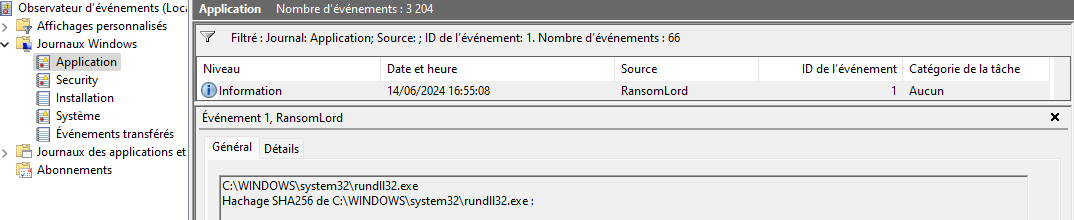
And also a level 15 alert in Wazuh (here in French) :
"rule": {
"firedtimes": 1,
"mail": true,
"level": 15,
"description": "Activation d'une DLL piégée par RansomLord sur XXXXXXX.local.XXXXXX.fr",
"groups": [
"RansomLord"
],
"id": "100057"